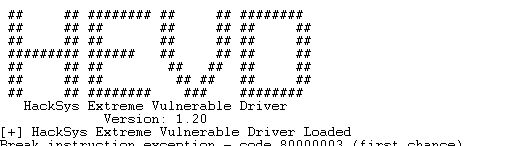Windows Kernel Exploitation With HEVD on x64 system
I Have been and still learning Kernel exploitation , and i found a very interesting Kernel driver HackSys Extreme Vulnerable Windows Driver filled with different bugs to help people who like to learn kernel exploitation a deep and easy way to understand that .
In this post we will focus on kernel stack overflow using C++ to write our exploit
ok so first things first we will devide this tutorial in 3 parts :
1- setting up our environment .
2- Discovering the bug and bsod the system .
3 - Writing the exploit and explotation :) .
PS: i’m still learning and there a big chance that i will make some mistakes or misunderstand some thing so don’t hesitate to point that if it is the case ;) .
Setting up our environment
For this tutorial i’m using a x64 Windows 7 , running on VMWARE and the x64 HEVD
Installing the Vulnerable driver
there is two way either compiling it or use the allready compiled one , i will chose the easy way (Compiled version)
you can download that from there github repo https://github.com/hacksysteam/HackSysExtremeVulnerableDriver/releases/download/v1.20/HEVD.1.20.zip
and we will be using OSR Driver Loaderto install HackSys Extreme Vulnerable Driver by browsing for the HEVD.sys and clicking on Regsiter Service .
you’ll see a “The Operation completed successfully” (Sorry mine it’s in french ;p).
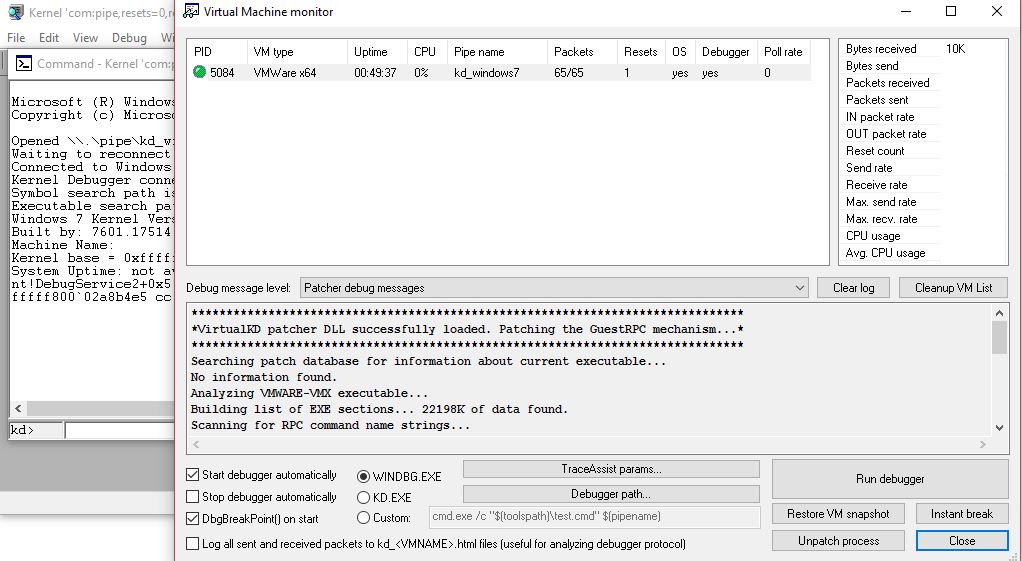
Now it’s time to setup the debugging environment , since this is a kernel exploitation the debugger must run remotely , for that we will be using the VirtualKD tool to help us just doing that , grab it from this link http://virtualkd.sysprogs.org/download/
after extraction in the VM you will have this
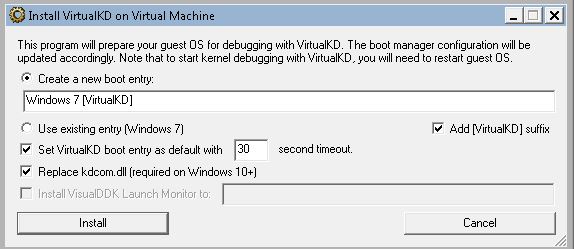
double click on the target folder then click on vminstall.exe you’ll get
click on install
cool everything seems fine , now before clicking on yes to restart , back to our host machine (NOT THE VM)
extract the same VirtualKD on the host machine click on vmmon64.exe restart the VM and you’ll get
make sure to check start debugger automatically or use Run debugger , then run the following command on Windbg to show up the HEVD driver debugging output
ed nt!Kd_DEFAULT_MASK 8
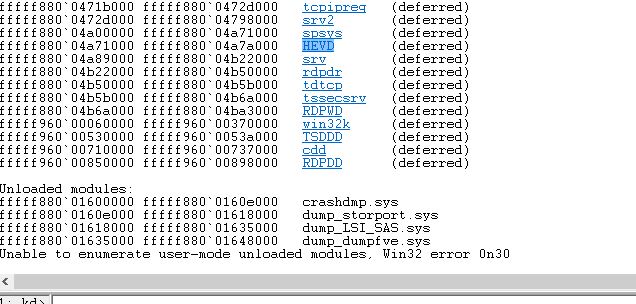
and also this to verify that HEVD has been installed
lm
if not type > g in windbg
repeat the first step to register the driver and click also on start service ,break and verify again
and you’ll get the follwing debugging output after starting the driver
Cool now we are ready to go to funny part :) .